A new wave of ransomware attacks is spreading across the world, paralysing banks, shipping corporations, oil companies and airports. IT Minister Ravi Shankar Prasad says that the impact on India has been minimal, noting that “India is not much affected at this stage.” The Indian Computer Emergency Response Team (CERT-In) has released an advisory on the ransomware attacks. One of the terminals in the nation’s largest container port, Jawaharlal Nehru Port Trust (JNPT) was affected by the malware, and the Ministry of Shipping stepped in to help tackle the situation.
The attack is strikingly similar to the global WannaCry ransomware attacks in May this year. Both attacks initially spread by spam email campaigns, spread across networks of organisations, encrypted the files on machines, prevented systems from being used, and demanded a ransom in bitcoin. The SMB vulnerability patched by Windows in the security bulletin MS17-010 was used to get into systems, along with the EternalBlue exploit that a hacking group known as the Shadow Brokers allegedly stole from a secret NSA server.
Mr. Tarun Kaura, Director, Product Management for Asia Pacific and Japan, Symantec notes that the ransomware attacks are getting increasingly sophisticated and following a predictable pattern. “Symantec’s Internet Security Threat Report 2017 revealed that Ransomware was one of the most significant threats facing both individuals and organizations in 2016. Attackers have honed and perfected the ransomware business model, using strong encryption, anonymous Bitcoin payments, and vast spam campaigns to create dangerous and wide ranging malware. While consumers in particular (69 percent of all infections) are at risk from ransomware, this year saw evidence that ransomware attackers may be branching out and developing even more sophisticated attacks, such as targeted ransomware attacks on businesses that involved initial compromise and network traversal leading to the encryption of multiple machines. In this latest attack, the ransom note is displayed on infected machines, demanding for $300 in bitcoins to recover files. According to available information Enterprise customers have been affected by this ransomware distribution campaign,” he said.
Mr. Kaura goes on to note the similarities between how, when and where the current malware and WannaCry spread, “one of the methods Petya uses to propagate itself is by exploiting the MS17-010 vulnerability, also known as Eternal Blue. Similar to what we saw during recent WannaCry attacks, there is also specific time zone and geo-spread that’s very familiar with WannaCry. It starts in time zones that wake up earlier and moves across as more people come online.” Both the ransomware attacks exploit the fact that systems have not been patched with security updates. The attack vector is similar, and also the methods used to paralyse the organisation from working normally.
Mr. Nilesh Jain, Country Manager (India and SAARC), Trend Micro said “Similar to WannaCry ransomware, the Petya ransomware exploits SMB vulnerability, passing through SMB protocol, and exploits vulnerability which lies in Microsoft Operating System. Companies who have been impacted should segment their infected areas from the rest of the network, so that it doesn’t propagate further. The problem is that, these kinds of ransomware attacks keep on coming and you cannot keep on patching the moment the attack comes in.”
There are also similarities in the kinds of targets picked by both the ransomware attacks. Mr. Rakesh Kumar Singh, Datacenter lead, Juniper Networks India says “We are seeing big impact at few of the Indian corporates and PSUs. Mainly corporates which are not in high-tech are more vulnerable as they have lots of legacy OS installations that were ignored as they were used for non-intensive purposes like data entry. We saw that lots of intellectual property data was locked out during the Wannacry event. Since Petya is not only exploiting the same ‘EternalBlue’ vulnerability but additional known vulnerability that was exposed from prior leaks, we are expecting a wider impact this time. We are also expecting that lots of home users would be affected too.”
Those organisations who had patched their systems in the wake of the WannaCry attack, will not be affected by the new ransomware because both the malware use the same vulnerabilities in the system. Mr. Srinivasan CR, Senior Vice President, Global Product Management and Data Centre Services, Tata Communications says “As the most devastating cyber-attack of 2017 to-date, the WannaCry attack has had a colossal impact on organisations around the world. The exploit infected over 200,000 computers in 150 countries, crippling everything from hospitals to logistics firms. Petya is very similar to WannaCry as it exploits the same vulnerability on Windows systems. Organisations that have updated patches for this vulnerability as issued by Microsoft in March 2017 should not have any further impact because of Petya.”
Mr. Srinivasan CR goes on to explain why some businesses may not be patching their systems. “Attacks such as the ones we have seen recently can be attributed more to the reason that software updates and patches do have an impact on applications in some cases. The level of cybersecurity readiness varies with the business. SMEs are at less risk compared to large corporations as their data is not distributed in most cases and if they get the basic security infrastructure like a firewall and windows update services they should be safe as long as they follow e-mail discipline. While businesses are aware and have up to date information on the latest patches through their security service providers, sometimes they take a conscious decision not to update to the latest patches immediately because of an ongoing business critical activity. You won’t be able to thwart every cyber-attack ahead of time but much like the game of chess, implementing a good strategy will always swing the odds in your favour,” he says.
Security researchers initially identified the ransomware as a variant of Petya, and the name has stuck. SecureList notes that the ransomware is being referred to as Petya, Petrwrap, NotPetya and exPetr. According to a statement by Kaspersky Lab, the ransomware is entirely new, “Kaspersky Lab’s analysts are investigating the new wave of ransomware attacks targeting organizations across the world. Our preliminary findings suggest that it is not a variant of Petya ransomware as publicly reported, but a new ransomware that has not been seen before. That is why we have named it NotPetya.”
The security experts suggest some solid measures that can be taken so that organisations can insulate themselves from such ransomware attacks. Backing up the critical data in air-gapped systems, continuously applying security patches to operating systems, and whitelisting of applications are some of the tactics that can be used to prevent infections.
According to Mr. Nilesh Jain, “To prevent the ransomware attack, firstly, companies should have proper segmentation of their network, most companies have horizontal network and there is no proper segmentation of network because of which the exploitation spreads very fast. The critical network and server should be properly segmented so that the penetration does not go beyond the segmentation of the network. Second thing is that companies must deploy host based intrusion firewall. They must enable firewall rule so that they can block the traffic coming from unknown sources. They also should make sure they patch the systems immediately.”
Mr. Srinivasan CR says, “Enterprises now realise that a strong security infrastructure is not just about a secure network, and investments need to be made in detection and predictive tools and services, and experienced personnel on standby to identify any weaknesses quickly. Industries and governments as whole will also continue to work towards policies and regulations that can safeguard against newer vulnerabilities that come with the rapid digital transformation of society”
“Regular patching of operating system is a must, not just on laptops/desktops but for all portable devices like mobile/tablets. Also it is a wakeup alert for all SMBs who avoided moving away from out-of-support operating systems. The main learning is that critical data should not be residing on user desktops. Cloud based solutions which ensures that the relevant data is made available to the user on demand but the storage of data itself is always on the cloud where it is easier to put security and anti-malware defenses,” according to Rakesh Kumar Singh.
Rana Gupta, Vice President of APAC Sales, Identity and Data Protection, Gemalto says, “Because data is the new oil in the digital economy, ransomware attacks that restrict access to important data until the attacker is paid are becoming increasingly common. However, neither businesses nor individuals should pay ransoms to unlock any files that have been affected by a ransomware attack, as this incentivises and rewards these kinds of attacks. In order to prevent becoming a victim of a ransomware attack, data should be backed-up and encrypted, and stored away from the network the rest of the data is stored on. This means that, in the event that a ransomware attack locks someone out of their files, they will have secure copies available. By doing this, the victim would be able to return to business-as-usual quickly and efficiently.”
The cybersecurity experts and CERT-In all agree on one thing, if infected, do not pay up the ransom. Paying a ransom is no guarantee that the files will be decrypted. The e-mail associated with the payment method has reportedly been shut down, so there is no way to decrypt the files.
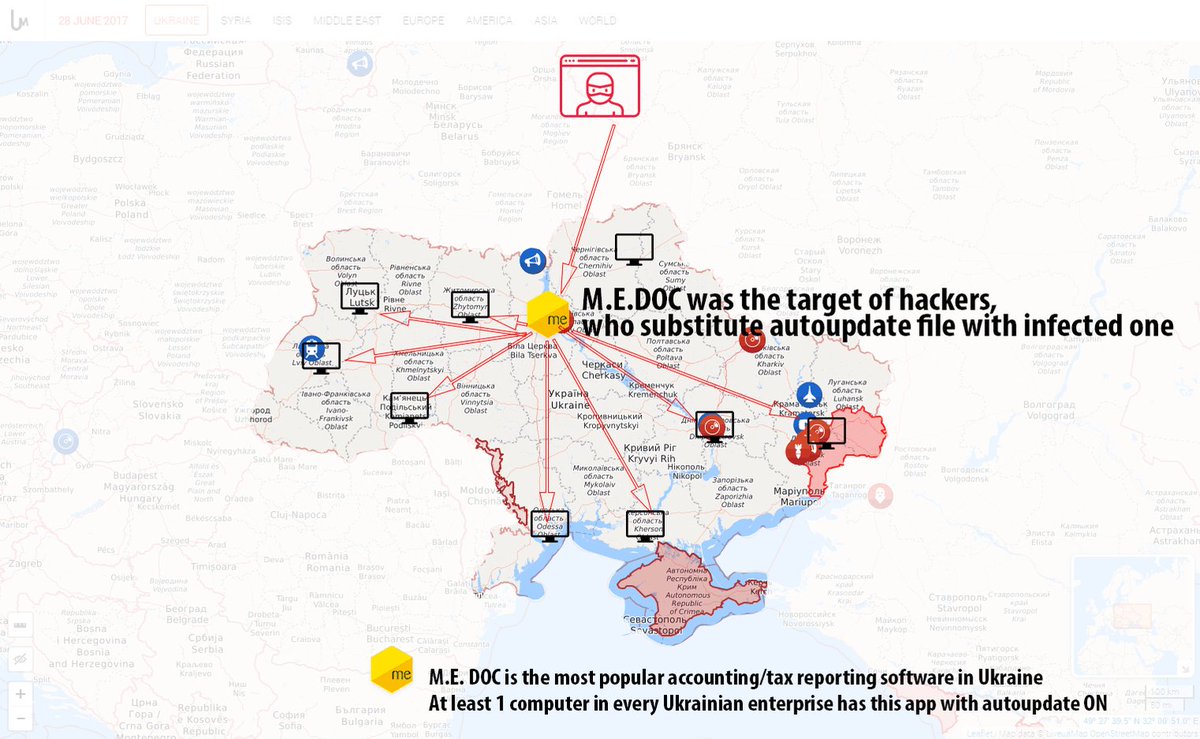
The actual ransom component on the malware does not seem to be the main priority, and could potentially be used to disguise a straightforward cyber attack to take down critical systems. In terms of where the attack was most drastic, Kaspersky telemetry suggests that Ukraine was the country most affected by the attack. According to the statement by Kaspersky Lab, “the company’s telemetry data indicates around 2,000 attacked users so far. Organizations in Russia and the Ukraine are the most affected, and we have also registered hits in Poland, Italy, the UK, Germany, France, the US and several other countries.”
We asked Mr. Jaspreet Singh, a Partner of the Advisory Practice, leading Cyber Security solutions at EY India, if any sectors were particularly affected by the attack. His response was, “It is not that particular sectors are vulnerable, but almost all sectors from telecommunications, banking, transportation, food/ beverages, power and utilities etc have all been affected.” When asked why the attackers were going after public utilities, Mr. Singh pointed out that “the impact would always be wider by going after public utilities. It is also about showing the capabilities of the attackers, we can bring down national critical infrastructure. The amount collected by the (WannaCry) ransomware is negligible compared to the media coverage it got. In fact, if you look at almost all ransomware cases across the globe before this, it is not always about the money. It is more about what is the impact you can create, about the hue and cry.”
The WannaCry attack raised a number of puzzling questions, and many of these same puzzling features can be seen in the new attacks as well. State sponsored groups are suspected to be behind both attacks. The malware was created by combining a number of other malware, including leaked tools allegedly created by the NSA. The intent appeared to be disrupting the critical infrastructures in countries, as against the actual collection of the ransom. The ransom is anyway typically not paid, and the systems created to collect it were among the less sophisticated components in the ransomware. These kinds of cyber attacks could be something far more sinister, disguised as ransomware attacks.
tech.firstpost







Comments
Post a Comment